<< All posts1 March 2024
Starting a thriving online business and creating an e-commerce site can be exciting. As long as you do it right, you will be on your way to building a successful business.
Unfortunately, this excitement to run a business makes entrepreneurs overlook the need for a secure website.
If you are one of them, do not worry. You are not a lost cost. There are still things you can implement to secure your online store. read more...
7 February 2024
In the vast world of the internet, there's a sneaky threat called a replay attack. It's like someone recording your secret handshake and using it to get into places they shouldn't.
Let's explore what replay attacks are, how they work, the risks they bring, and how you can stay safe with a trustworthy VPN read more...
18 January 2024
Hackers don’t limit their attacks to e-commerce sites. Blogs are vulnerable as well. WordPress and other suites are so popular that cybercriminals make it their business to learn how to exploit any weaknesses.
When they find those openings, they might take your site hostage, redirect your visitors to nefarious websites, or retrieve sensitive data about your business or customers.
In any case, it’s imperative that you ensure your blog is locked down. You can start this process by checking out the following security tips. read more...
18 September 2023
The financial world is experiencing a transformation, as AI-powered fraud detection systems begin to take center stage in securing transactions. With the rise of digital payments, the threat of fraud has escalated, leading to the integration of intelligent solutions that adapt and learn.
Unlike traditional methods that often fall short in the dynamic landscape of financial fraud, AI’s ability to analyze vast amounts of data in real-time is revolutionizing the way financial institutions detect and prevent fraudulent activities.
This post explores this growing phenomenon, including the surprising role of VPN in enhancing these security measures. read more...
12 August 2023
Remember that moment when you received an email from your 'bank' urgently asking for your account details? Or perhaps when you clicked on a link, expecting to land on your social media page, only to be greeted with an uncannily similar but subtly off version of it?
If these experiences sound familiar, you've had a brush with the silent but dangerous specters of the internet - phishing websites. Like a detective searching for clues, spotting a phishing website requires a keen eye for detail and understanding their sly tricks.
Let's unravel the key signs that can help you expose these digital impostors. read more...
13 July 2023
Everybody knows that cybersecurity plays a pivotal role in safeguarding our online existence. It is imperative to adopt proactive measures that shield us from potential threats. With the relentless surge in cyber attacks, bolstering our cybersecurity awareness has assumed paramount importance.
Let's delve into 15 invaluable tips that will empower you to fortify your online safety, ensuring the utmost protection for your sensitive information. read more...
5 May 2023
It's common knowledge that technology has drastically changed how people live, becoming the norm of today's era—from mobile devices that allow users to interact with long-distance loved ones and friends to smart technologies that offer convenience to those residing in homes. Similarly, many organizations have benefited from various technologies.
If you're an organization, another promising technology that can protect you online is robotic process automation (RPA).
RPA is a technology that imitates human actions in handling repetitive, high-volume, and rule-based tasks, playing an efficient role in finishing these uneventful and monotonous tasks that are more suitable to be performed by computers. As a result, it frees up time for individuals to do other activities that require creativity, strategy, and innovation.
Lets see how it can become the future of cybersecurity. read more...
17 March 2023
In today's world, cyber security threats are a significant business risk. With the increasing reliance on technology and digital infrastructure, organizations must be prepared for any potential cyber threats that may arise. Hence, companies of all sizes must take preventative measures against these attacks.
Enterprises may suffer financial losses, reputational damage, and even criminal liability without adequate protection. By taking preventative action now, you will have peace of mind, knowing you're doing everything possible to keep your business's data safe from external threats. Moreover, investing in reputable service providers in your location can proactively protect your company.
We will explore how to prepare your business against cybersecurity risks and threats by providing an overview of best practices without compromising operations productivity or efficiency. read more...
17 February 2023
Cybersecurity has become and will continue to be an increasingly significant part of our lives. The risks presented by cybercriminals are growing along with the rapid advancement of technology.
Let's discuss the growing need for cybersecurity, the trends the future holds, and solutions to ensure a desirable and secure future. read more...
19 January 2023
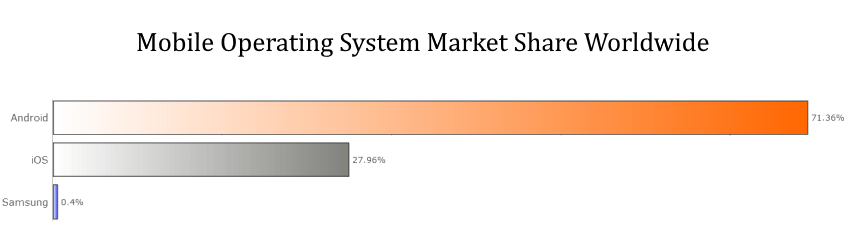
When you are looking to enhance the security of your personal smartphone the results can be very different depending on which operating system you are using.
Yes, because despite ever-improving technological advances that help to strengthen security, cyber criminals are also keeping up and attacking our data and networks in a myriad of novel and elaborate ways.
Therefore, if you want to stay ahead of the game, it’s time to review two of the most popular operating systems in the world and find out which one is the best and most secure, both for your personal data and for your business.
Who is the winner of the all-time OS security war — Apple or Android? Learn more in our comparative guide. read more...