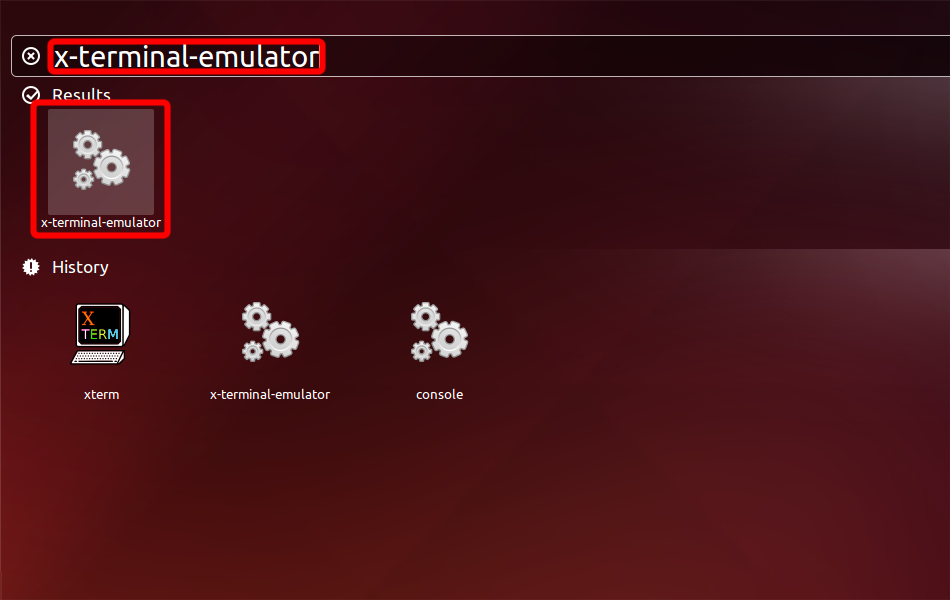
Exécuter l’émulateur de terminal : Appuyez sur Alt+F2 sur le clavier, tapez x-terminal-emulator et appuyez sur Entrée.
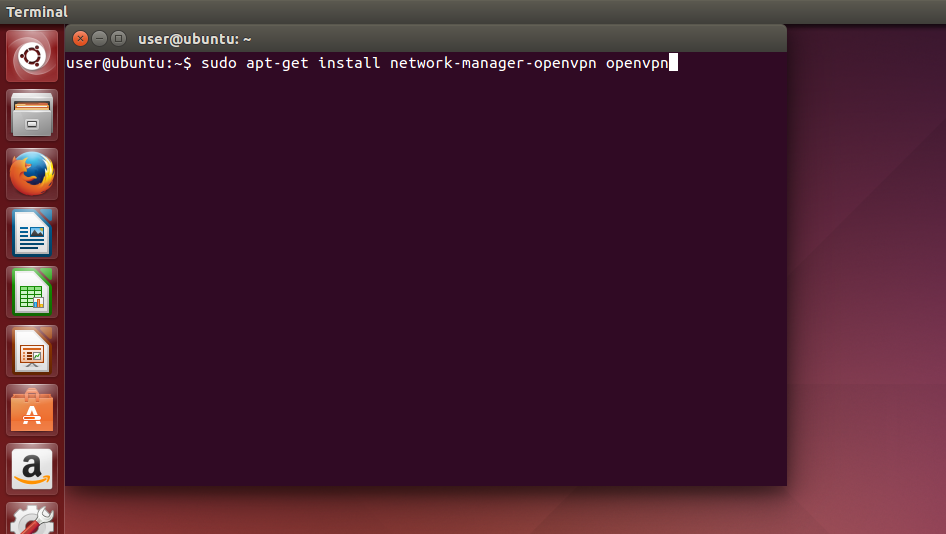
Installez OpenVPN avec la commande suivante.
sudo apt-get install network-manager-openvpn openvpn
For Ubuntu 16.04 install also network-manager-openvpn-gnome
sudo apt-get install network-manager-openvpn-gnome
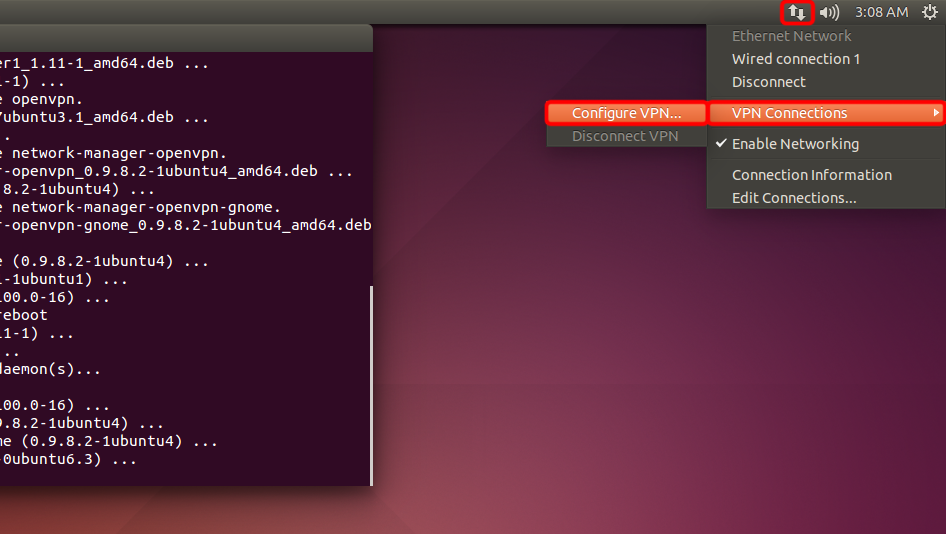
Ouvrez le menu réseau, allez dans « Connexions VPN » et cliquez sur « Configurer le VPN... ».
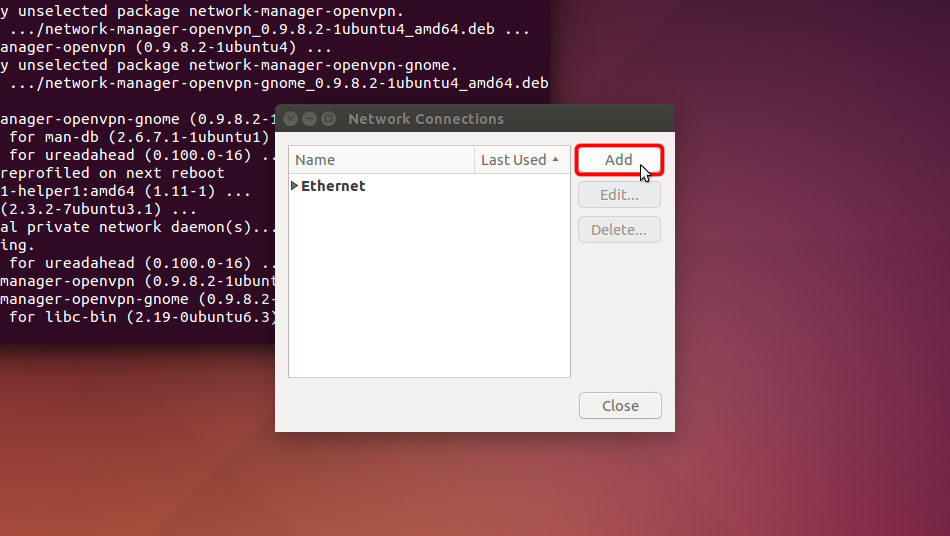
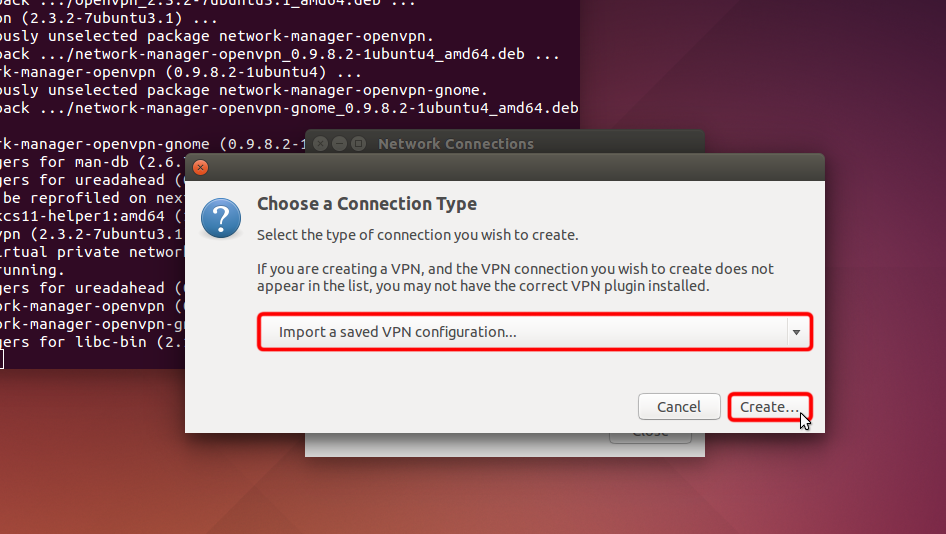
Cliquez sur « Ajouter ».
Cliquez sur « Importer une configuration VPN enregistrée... » et cliquez sur « Créer »
Téléchargez le fichier de configuration OpenVPN (fichier .ovipn), sélectionnez la section « Téléchargements » et ouvrez le fichier Trust.Zone-VPN.ovpn en double-cliquant dessus.
Fichier OpenVPN (.ovpn): Caché. Connectez-vous ou inscrivez-vous pour voir.
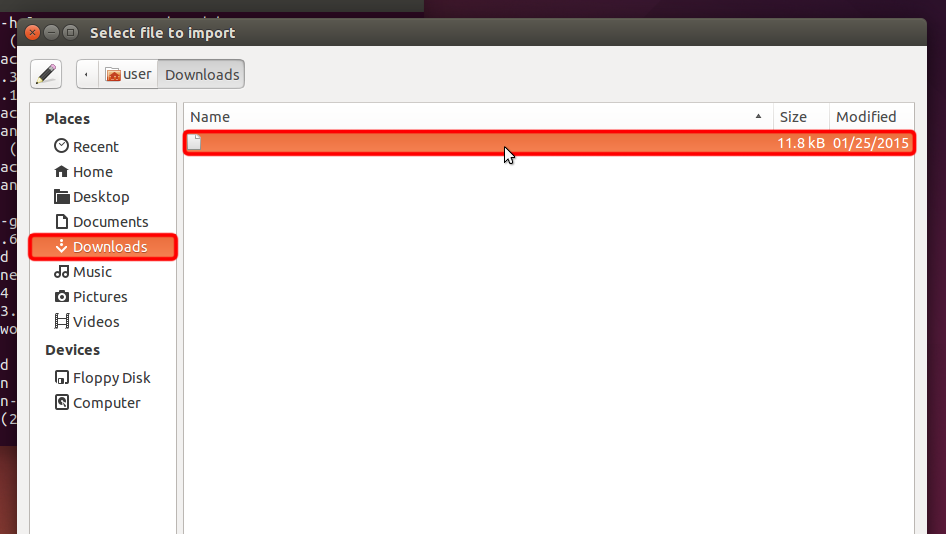 Trust.Zone-VPN.ovpn
Trust.Zone-VPN.ovpn
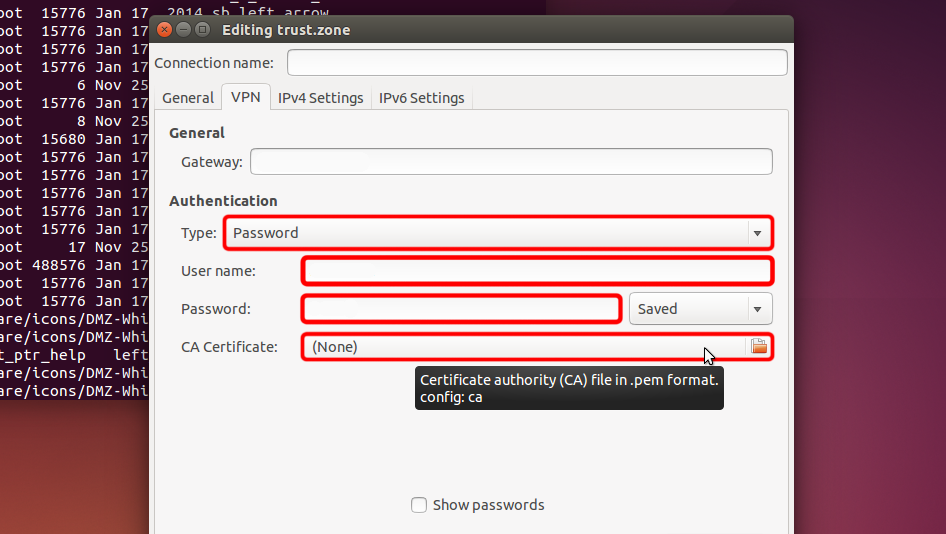
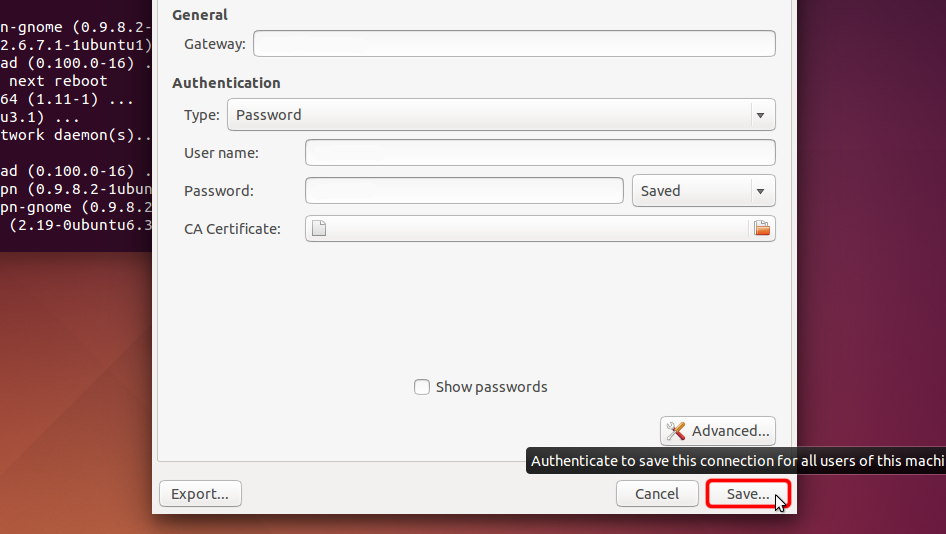
Sélectionnez « Mot de passe » dans le menu déroulant « Type », entrez votre nom d’utilisateur et votre mot de passe VPN.
Your VPN Username: Caché. Connectez-vous ou inscrivez-vous pour voir.
Your VPN Password: Caché. Connectez-vous ou inscrivez-vous pour voir.
Téléchargez le fichier de certificat et cliquez sur le sélecteur de fichier « Certificat CA » pour choisir le fichier de certificat.
Certificate file: Caché. Connectez-vous ou inscrivez-vous pour voir.
 Trust.Zone-VPN
vpn.trust.zone
Trust.Zone-VPN
vpn.trust.zone
Naviguez jusqu’à « Téléchargements » et double-cliquez sur le nom du certificat pour le choisir.
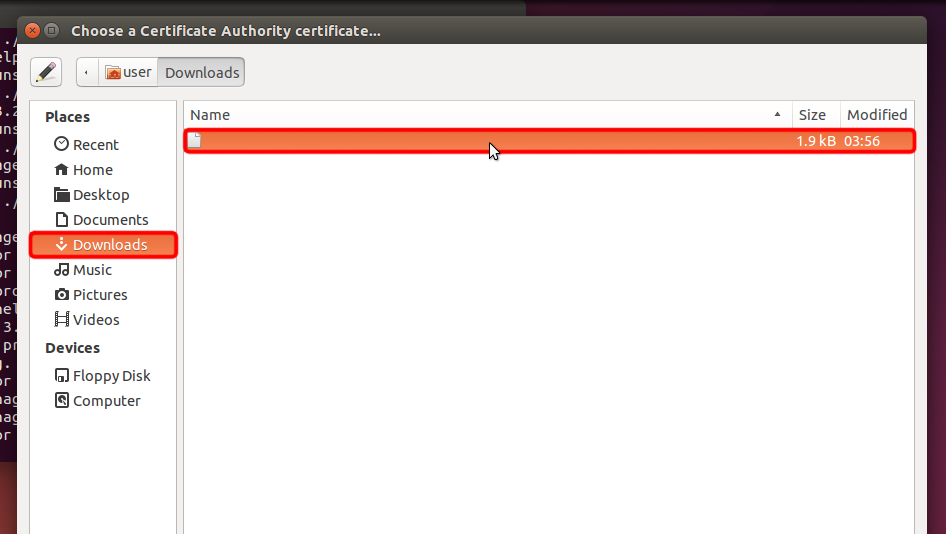 Trust.Zone-VPN.pem
Trust.Zone-VPN.pem
Cliquez sur « Enregistrer... » afin d’enregistrer les paramètres de connexion VPN.
 vpn.trust.zone
Trust.Zone-VPN.pem
vpn.trust.zone
Trust.Zone-VPN.pem
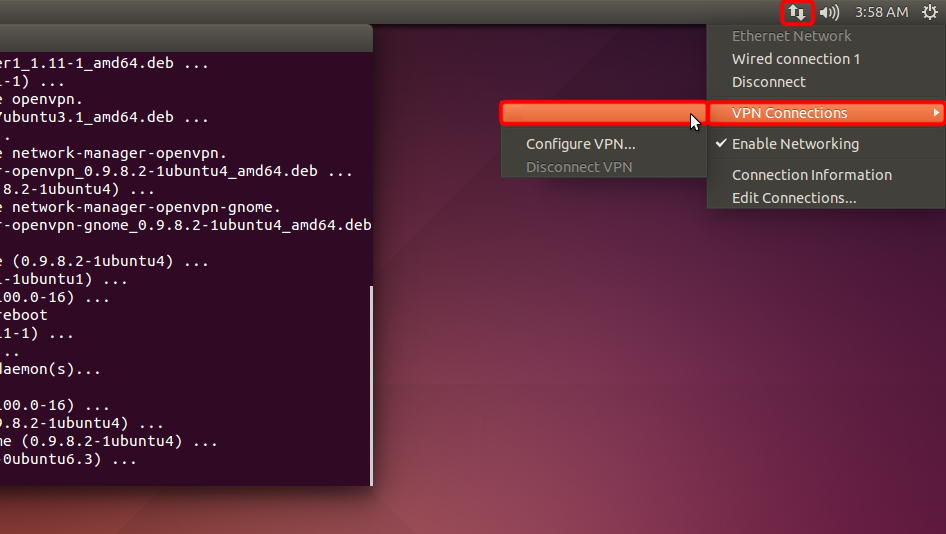
Cliquez sur l’icône du menu réseau, choisissez « Connexions VPN » et cliquez sur le nom de votre connexion créée pour établir une connexion VPN.
 Trust.Zone-VPN
Trust.Zone-VPN
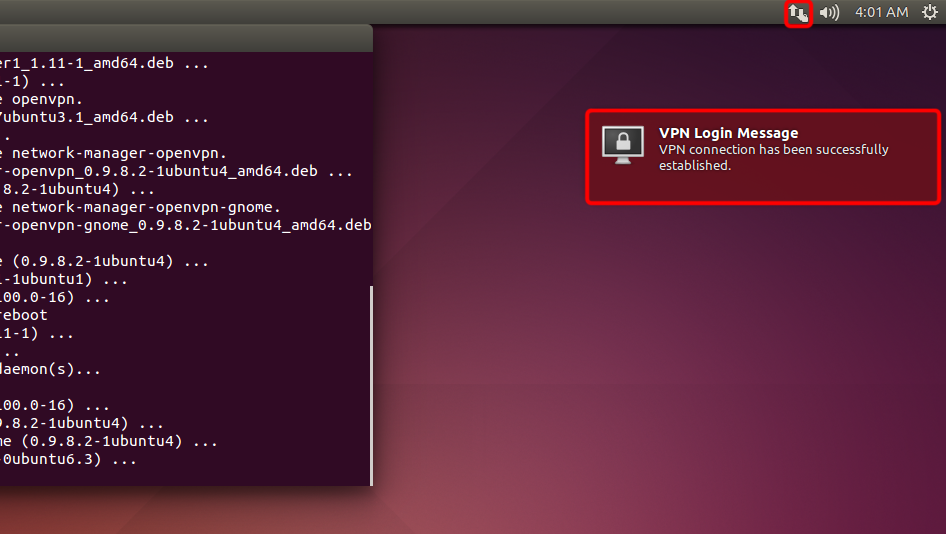
Si la connexion a été établie avec succès, l’état s’affiche dans la barre de menu et dans un message en forme de bulle.
Afin de gérer vos connexions VPN, cliquez sur l’icône « Connexions réseau », choisissez « Connexions VPN » => « Configurer VPN... ».
Une fois connecté au VPN Trust.Zone, votre adresse IP IPv4 change, mais votre adresse IPv6 reste la même.
Ce n’est pas un problème si votre FAI ne prend PAS en charge IPv6, mais si c’est le cas, votre adresse IPv6 peut fuir.
La meilleure façon d’empêcher IPv6 de fuir est de désactiver IPv6 dans votre distribution linux. Voici comment vous pouvez le faire.
Pour vérifier si IPv6 est déjà désactivé, exécutez la commande suivante :
cat /proc/sys/net/ipv6/conf/all/disable_ipv6
Si la commande renvoie 1, IPv6 est déjà désactivé et vous pouvez ignorer les étapes ci-dessous. Si la valeur de retour est de 0, veuillez suivre les instructions ci-dessous :
Veuillez ouvrir le fichier /etc/sysctl.conf dans votre éditeur de texte préféré. Dans notre exemple, nous utiliserons nano editor.
sudo nano /etc/sysctl.conf
Ajoutez les lignes suivantes à la fin du fichier :
net.ipv6.conf.all.disable_ipv6 = 1
net.ipv6.conf.default.disable_ipv6 = 1
net.ipv6.conf.lo.disable_ipv6 = 1
Vous pouvez maintenant enregistrer le fichier et quitter l’éditeur. Si vous utilisez nano, vous devez appuyer sur Ctrl-O pour écrire les modifications et appuyer sur Entrée pour confirmer l’écriture du fichier. Ensuite, vous pouvez appuyer sur Ctrl-X pour quitter l’éditeur.
Exécutez la commande suivante pour mettre à jour les paramètres du noyau :
sudo sysctl -p
La commande renverra les lignes que vous avez ajoutées à /etc/sysctl.conf
Maintenant, lorsque vous exécutez cat /proc/sys/net/ipv6/conf/all/disable_ipv6 la commande doit renvoyer 1. Cela signifie que IPv6 est désactivé, donc la fuite IPv6 n’est plus possible.
Ouvrez la Page Oprincipale de Trust.Zone et rechargez-la si elle est déjà ouverte afin de vérifier si votre connexion avec le VPN Trust.Zone est correctement établie.
Vous pouvez également visiter notre Page de Vérification de Connexion.
 Votre IP: x.x.x.x ·
Votre IP: x.x.x.x ·  Danemark ·
Votre emplacement réel est caché!
Danemark ·
Votre emplacement réel est caché!