VPNs are becoming more important with each day that passes because of bloodthirsty cyberattackers that feed on a digital trace left on the internet. There might also be information you would like to upload or send to someone without it being intercepted by your ISP.
There are different types of VPNs and to use them effectively, you should know how each one applies in which situations:
Client-based VPNs are the most common type of private networks that connect consumers to a remote network. These client-based connections are made on a client application, software, or web app. That client software takes care of connecting the user and securing his connection link to the internet.
When establishing this connection link to the remote network, it is encrypted to secure all traffic transmitted through that Virtual Private Network. This eliminates the need to set up a VPN server before connection because everything is preset and it is basically plugged and play. All you have to do is download that client VPN, fill out the required details, and then you'll be all set to start using it.
A client-based VPN is a very common Virtual Private Network with normal everyday applications such as protecting you from attacks that were perpetrated on public networks like Wi-Fi.
The secure networks also protect your geographical location by using IP masking technology. Thus, a client-based virtual private network is most suitable for ordinary citizens requiring online anonymity and security, especially in public networks.
Network-based VPNs are one of the complex virtual private network models because develop them entails connecting different networks on an unsecured network. They are common mostly amongst large companies with operations based in different cities, states, countries, or even continents. For both branch offices to have the latest information, a secure link has to be created for uploads and downloads on both ends.
The easiest option might seem to be linking both these networks using internet protocols. Although this might appear to be very efficient if your network is insecure, it can leak information like a sieve.
To avoid this from happening, network-based VPNs create a secure link for companies to share information privately using unsecured networks with the intention of linking geographically dispersed offices.
Companies that use remote desktop sessions also benefit a lot from network-based VPNs. The VPN will prevent anyone without authorization to access that session and create tunnels to restrict the traffic coming through. They can unify their working software across all branches in a highly secure manner allowing more productivity without compromising security.
Remote access virtual private networks are much similar to client-based systems but they are mostly used by companies instead of individuals. They are provided as a SaaS system providing cloud-based support and this reduces the setup costs of servers and all the equipment needed to establish a secure network.
Remote access VPNs help businesses outsource their secure network requirements remotely instead of doing it all in-house. That benefits the company by reducing costs exponentially including those of managing and maintaining servers. At the same time, it does not compromise security protocols because all internet activity will be safeguarded from prying eyes.
Getting a remote access VPN for your business is very easy and it goes a long way into securing intellectual property, customer information, and other sensitive data. A lot of businesses that share an office building, including amenities such as Wi-Fi, use remote access virtual private networks.
There are two reasons for this. They do not have to rent more offices to set up servers or get their own internet access, which could also create a loophole for attackers.
Similar to network-based VPNs, site-to-site Virtual Private Networks also help connect large corporations. These connections can come in two different forms, which are an intranet or extranet connection. When choosing between the two, it greatly depends on what type of networks you would like to connect.
For example, if you would like to connect different offices of the same business, an intranet VPN connection can be much suitable. That is because your network infrastructure would be similar and it will have an internal design. Whereas, linking the network with another external one involving trade partners and other companies should be done using an extranet.
An extranet connection will link authorized external networks to access yours and share information as well as documents. You can connect various local area networks into one, allowing both parties to work together in a controlled, secure, and private environment. An extranet also protects the intranets of those two parties and creates a safe space that does not infringe on the privacy policies of either party.
Amongst VPN technology, there are quite a number of variations with different specialties. The protocols a client-based or remote access VPN uses dictate its features. When a virtual private network uses more protocols, its features are highly advanced and can tackle an additional amount of tasks.
For example, a multi-protocol VPN can be used for a variety of features such as improving video streams, eliminating censorship, and any other blocks. Some of the most common protocols used by virtual private networks include SSL/TLS encryption, IKev2/IPSec, and others. Other VPN systems use their own proprietary protocols. Proprietary protocols are highly customized and can tackle very high-end tasks.
Double VPN is another way to secure your connection. With Double VPN your IP address is replaced twice. It forwards your encrypted traffic through two VPN servers instead of one.
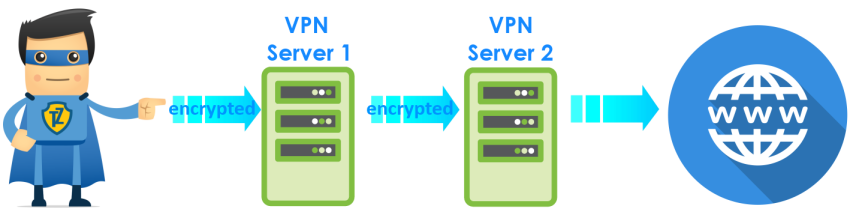
A client-based or remote access VPN is not that advantageous if it uses only one protocol. Whereas, a single-protocol network can be more suitable for large companies establishing an intranet or extranet specific to a certain task.
Choosing which type of network should be implemented for companies will depend greatly on your operations. For end-users, multi-protocol networks are robust and much more reliable and fast because they offer customers almost everything they need to be safe on public networks.
Although a no-logging VPN is not specifically a type of virtual private network, it is another major differentiating factor amongst them. There are VPNs that log history searches and those that keep zero logs. When choosing a client-based app or remote access private network, you should consider this.
Try to understand the logging policy. If their policy specifies that there will be no logging of sensitive data entailing to your connection session or bandwidth. These no-logging policies outline that none of this information will be collected, stored, or shared.
A VPN with this policy usually operates from an area where no-logs are permitted. Examples of these jurisdictions include Panama, Seychelles, Romania, and the British Virgin Islands. For example, Trust.Zone VPN Service is located in Seychelles, under offshore jurisdiction.
There are a lot of different types of VPNs that you can choose from depending on whether you’re using it for commercial purposes or personal use. A lot of virtual private networks used for personal use are called client-based applications and generally have multi-protocols. Larger companies have a variety of options that they can explore depending on their requirements. If a business has to connect its network with others, they can use an extranet. In the case where they would like to connect their offices to one network, an intranet connection is a much better position.
Author Bio:
James Murphy is a full-time content creator from New York currently working for Best essays where he provides best assignment writing service to research students. His work includes essays, thesis, and dissertation in science and engineering subjects. He is a father of two lovely toddlers and is a die-hard fan of the New York Yankees.