28 Ноября 2024
Are you planning to shop for Black Friday online this year?
Millions of people take part in Black Friday shopping to save a ton of money. That’s why it’s so important to protect yourself from online fraudsters and identity thieves this holiday season.
If you don’t have a VPN to protect your identity while you shop, you’ll be exposed to all sorts of security issues and identity theft. That means your credit card information could be stolen, your location could be tracked, and your browsing history could be seen by advertisers and other hackers.
Besides, VPN allows you to get lower prices during Black Friday for your favorite products online by replacing your original location. подробнее...
1 Ноября 2024
SOCKS5 is a secure proxy protocol that routes internet traffic through a server, masking the client’s IP address.
It supports both TCP and UDP traffic, providing flexibility for various applications like web browsing, streaming, and P2P. SOCKS5 does not encrypt traffic by itself but adds authentication features, which helps prevent unauthorized access.
It is lightweight and faster than other VPN protocols, as it doesn't add encryption overhead, making it suitable for low-latency applications where privacy is needed but full encryption isn’t essential.
Here is a guide how to set up SOCKS5 with TrustZone подробнее...
1 Ноября 2024
Shadowsocks is a secured SOCKS5 based protocol designed for censorship evasion. It uses strong encryption (like AES-256-GCM or Chacha20) and traffic obfuscation to bypass deep packet inspection, making it harder for firewalls to detect.
Unlike other VPN protocols, it only routes selected traffic, resulting in lower latency and higher speeds, ideal for accessing restricted content in high-censorship regions.
Here is a guide how to connect to TrustZone VPN servers using ShadowSocks protocol. подробнее...
31 Октября 2024
Halloween magic is already in the air!
Find your treats with our special deals. Get your thrilling savings NOW!
Get 1 YEAR of FREE VPN protection and stay safe from the scariest threats online. подробнее...
17 Октября 2024
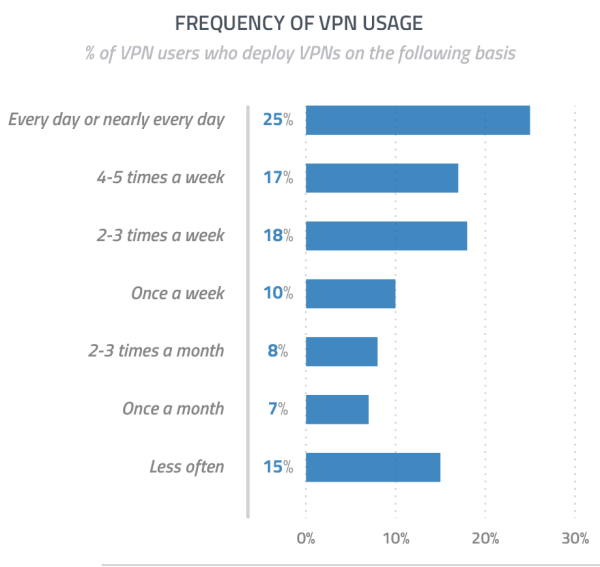
1 in 4 VPN users accessing daily – according to new report by GlobalWebIndex. The main question of the survey was “How frequently do you use VPNs to connect the Internet?
At least, 10% of VPN users access VPN once a week. 7% - once a month. Report was presented by GlobalWebIndex Web Analytics Company. подробнее...
20 Сентября 2024
International human right organizations have been expressing concern about how Russian authorities have been repressing free press for years. Instead of improving, the situation has gotten worse and worse until censorship involved the Internet as well.
With the Ukraine invasion, furthermore, censorship in Russia has reached levels never seen before: Russian citizens can’t access thousands of websites and new ones are being obscured every month.
According to the latest report, VPN usage in Russia increased by 900%
When it comes to online restrictions, however, there is a way of getting around them, and in this article, we’re exploring how. подробнее...
19 Сентября 2024
VPNMentor, the leading VPN comparison service has recently compared the 200+ VPNs on the web to choose the best VPN with dedicated IP addresses.
VPNMentor has rated TrustZone as #2 in the list of the Best Dedicated IP VPNs. подробнее...
18 Августа 2024
In certain regions, accessing X (formerly known as Twitter) can be challenging due to government-imposed restrictions. Trusted VPN services offer a reliable solution to bypass these blocks, enabling you to connect to X securely and privately.
Here’s a detailed guide on how to use TrustZone VPN to unblock X. подробнее...
2 Августа 2024
In recent times, access to Instagram has been restricted in Turkey, causing frustration among many users who rely on the platform for communication, entertainment, and business. Turkey has blocked Instagram as part of broader internet censorship measures following specific events and due to ongoing regulatory and political pressures.
The legal amendments to Turkey's internet laws have compelled social media companies to comply with government demands, under threat of severe penalties, including service throttling or outright bans. This regulatory environment has led to increased censorship and has put pressure on platforms like Instagram, Facebook and Twitter to conform to these regulations to avoid disruptions.
For users in Turkey who want to unblock Instagram, using a VPN like Trust.Zone can be an effective solution. Here’s a step-by-step guide подробнее...
30 Июля 2024
The Olympic Games are an event watched by millions around the world. However, due to regional broadcasting restrictions, some viewers might face difficulties accessing their preferred coverage. A Virtual Private Network (VPN) is a powerful tool that can help bypass these restrictions, providing a seamless viewing experience.
Here’s a comprehensive guide on how to watch the Olympic Games 2024 in Paris using a free VPN. подробнее...